Originally Published by Chris Welsh – Housley Instructor
Goodbye to VLANs. Well… not quite
Cisco ACI Tutorial – Part 2
ACI does not use VLANs or even subnets to isolate policy groups. I’m sorry if this is a shock for you, but before I discuss how policy groups are bound by an object known as an End Point Group I’ll use this tutorial to take you through the replacement concepts for VLANS and IP addressing. The containers used by ACI to provide IP addressing isolation are the Tenant, and the Private Network. Bridge Domains are used to provide multicast and broadcast isolation (similar to VLANs) and you’ll be pleased to know that we still use Subnets for IP addressing.
In this part of the tutorial I am going to take you through the configuration of the primary containers in ACI as you setup a Tenant, a Private Network, two Bridge Domainsand two Subnets.
TIP: |
If you have not read Cisco ACI Tutorial – Part 1, now would be a good time. It contains a diagram of the topology and some important notes about conventions used. |
First a little theory
ACI uses the concepts of Tenants, Private Networks, Bridge Domains, and Subnets in a hierarchy to contain routed traffic. Note that the concept of VLANs is entirely absent. Later I will add the most important policy containment concept, End Point Groups (EPGs) to the mix.
This diagram shows the hierarchy of Tenants, Private Networks, Bridge Domains, and Subnets.
Note that some relationships are linked such as Bridge Domains, which are linked toPrivate Networks, while others are parent-child relationships, such as Subnets, which are children of Bridge Domains which in turn are children of Tenants. Note that these relationships are also one-to many – a Tenant may have multiple Private Networks,Private Networks can be linked to multiple Bridge Domains, and Bridge Domainsmany multiple child Subnets.
Note: |
Typically you will have only one Subnet per Bridge Domain, so in that sense a Bridge Domain “resembles” a VLAN, and a Subnet “resembles” a VLAN interface. |
The naming and numbering of the items also reveals some of the isolation as well. Note that the names BD1 and BD2 have been used in each Tenant, and that Tenant Largehas three Private Networks (VRFs), two of which have an instance of the 10.1.1.1/24subnet associated with it.
Configuration Steps
Step 1: Add a new Tenant
A tenant is a logical container for application policies that enable an administrator to exercise domain-based access control. A tenant represents a unit of isolation from a policy perspective, but it does not represent a private network. Tenants can represent a customer in a service provider setting, an organization or domain in an enterprise setting, or just a convenient grouping of policies. [From ACI Help]
A Tenant is a logical container for isolating routing and switching functions. A Tenant will require at least one Private Network to provide routing functionality, and at least one Bridge Domain to provide layer 2 isolation. [RedNectar’s Definition]
TENANTS > ADD TENANT
- Name: RedNectar
A private network is a layer 3 context (a VRF) that provides IP address space isolation for tenants. Each tenant can have one or more private networks, or share one default private network with other tenants when there is no overlapping IP addressing being used in the ACI fabric. [From ACI Help. I added the emphasis to illustrate how the terms private network, [layer 3] context and VRF are used interchangeably in ACI terminology]Step 2: Give the new Tenant a Private Network
TENANTS > RedNectar > Tenant RedNectar > Networking > Private Networks
- (+) Create Private Network
| Note:
|
The Create Private Network option is reached by right-clicking on the Private Networks element in the Navigation Pane or by clicking the ACTIONS menu at the top right hand side of the Work Panel |
- Step 3: Give the new Tenant two Bridge DomainsName: VRF1
- Create A Bridge Domain [ ] Unchecked
A bridge domain represents a L2 forwarding construct within the fabric. One or more EPG can be associated with one bridge domain or subnet. A bridge domain can have one or more subnets associated with it. One or more bridge domains together form a tenant network. [From ACI Help]
A Bridge Domain is a Layer 2 (broadcast) domain that must be associated with a Tenant‘s Private Network. A Bridge Domain may contain one or more Subnets that can provide routing services for associated End Point Groups. [RedNectar’s Definition]
TENANTS > RedNectar > Tenant RedNectar > Networking > Bridge Domains
- (+) Create Bridge Domain
- Name: Clients-BD
- Network: RedNectar/VRF1
- (+) Create Bridge Domain
- Name: PublicServers-BD
- Network: RedNectar/VRF1
Step 4: Give the new Bridge Domains a Subnet each
A subnet, which represents routes that will be exported. While a context defines a unique IP address space, that address space can consist of multiple subnets. These subnets are defined per bridge domain. A bridge domain can contain multiple subnets, but a subnet is contained within a single bridge domain. [From ACI Help]
A Subnet is defined by an IP address/mask and provides a routing gateway service for End Point Groups that are associated to the Subnet‘s parent Bridge Domain. A Bridge Domain can contain multiple Subnets, but a Subnet is contained within a single Bridge Domain. [RedNectar’s Definition]
TENANTS > RedNectar > Tenant RedNectar > Networking > Bridge Domains >Clients-BD > Subnets
- (+) Create Subnet
- Gateway IP: 192.168.10.1/24
TENANTS > RedNectar > Tenant RedNectar > Networking > Bridge Domains >PublicServers-BD > Subnets
- (+) Create Subnet
- Gateway IP: 203.0.113.1/24
- Scope:
[ ] Private Subnet [Unchecked]
[x] Public Subnet
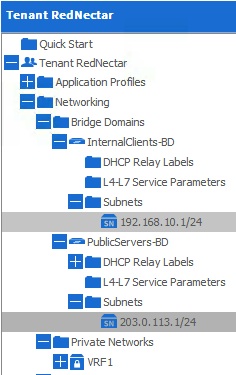
Step 5: Verify your configuration
Navigate your way around the Navigation Pane and expand the relevant sections to verify that you have. It should look something like this:
And diagrammatically, it could be represented like this:
Discussion
Note that you have created a structure to contain your subnets that does not involve VLANs. If you have come from a networking background, this will be a foreign concept for you. Subnets are however contained by another scope called a Bridge Domain. In many ways a Bridge Domain is similar to a VLAN, but is not a container for policy enforcement. For Policy enforcement, you will need to sing a new song for sorting server groups and policy, namely Application Profiles and End Point Groups.
RedNectar
Note:  |
If you would like the author or one of my colleagues to assist with the setup of your ACI installation, contact learning@housley.com.au and refer to this article. Housley works mainly around APJC, but are not restricted to this area. |
Footnotes
| Quotations: | The quotations supplied to describe the various elements are taken directly from the ACI Help. I did not write this content and want to be clear about the source. Which also should give you a heads up: It is a good idea to click the little i symbol in the top right-hand corner of many panes and dialogues. |
| Naming Conventions: | Note also the naming convention used. You will find that I almost always give an object a descriptive name followed by a dash followed by an identifier – such as Clients-BD – the name only has one dash. If a separator is needed in either part of a name, a dot . or a colon : or an underscore _ is used. Sometimes a generic name is appropriate, especially if the purpose is not clear (you CAN’T change names later). If I had have planned multiple VRFs (Private Networks) I may have named them something like DMZ-VRF and Internal-VRF, but in this case I chose a generic VRF1 as a name. |